How to Protect Your Data from Ransomware Attacks in 2025

Table of Contents
- How to Protect Your Data from Ransomware Attacks in 2025
- The Rising Threat Landscape in 2025
- Core Strategies for 2025 Ransomware Protection
- Cloud Data Solutions for Ransomware Prevention
- Secure Backup & Recovery Methods
- Frequently Asked Questions
- What’s Next; Acting with Purpose
- Ready to strengthen your ransomware defenses?
Ransomware has shifted from headline-making chaos to a day-to-day threat. In 2025, attackers are faster, smarter, and increasingly opportunistic. For businesses, the cost of inaction is too steep.
This post lays out ransomware protection 2025 strategies: how to harden defenses, design backups, deploy cloud-based protections, and stay compliant under evolving regulations. We’ll also walk you through frequently asked questions so you can see what’s changing and what still works.
The Rising Threat Landscape in 2025
What’s New in Ransomware Tactics?
- Shorter windows, faster strikes: Attackers now often launch full-scale ransomware within hours of initial access. Veeam reports that the “breakout time” (from compromise to lateral movement) can collapse to under 48 minutes and in extreme cases as little as ~51 seconds.
- Ransomware-as-a-Service (RaaS) is more pervasive: Criminal groups now offer plug-and-play ransomware toolkits, lowering the barrier for entry.
- Extortion via data theft, not just encryption: Instead of (or in addition to) encrypting your files, attackers exfiltrate data and threaten public leaks. Veeam notes that data exfiltration attacks are increasing.
- AI-empowered attacks: Some emerging ransomware models use large language models (LLMs) to adapt on the fly, write custom payloads, or orchestrate attacks dynamically. AI in data security is now both a weapon for attackers and a critical layer of defense for organizations.
- More targets among SMBs and critical sectors: According to Splunk, attackers increasingly aim at small- and medium-size businesses because their defenses tend to be weaker.
The numbers back it up: the first quarter of 2025 saw a 213% increase in reported victims compared to Q1 2024. Meanwhile, Sophos’s State of Ransomware 2025 shows that many organizations still fall victim due to exploited vulnerabilities and lack of staff or skills.
So: defenses that were once adequate may no longer be sufficient.
Core Strategies for 2025 Ransomware Protection

Layered Defense Is Non-Negotiable
One defensive measure alone no longer suffices. Instead, combine:
- Strong access controls and identity management enforce multi-factor authentication, zero-trust segmentation, and least privilege.
- Behavioral and threat analytics Use AI and anomaly detection to flag suspicious activity before encryption begins. This is where AI in data security and AI-driven security services can drastically reduce response time.
- Network segmentation contains lateral movement so if one area is hit, the damage doesn’t spread freely.
- Endpoint protection + EDR/XDR systems modern tools detect suspicious file behavior or encryption patterns.
- Honeypots and deception trick attackers into “fake” data to reveal intrusion paths without exposing real assets.
Veeam’s best practices guide highlights that prevention, early detection, and clean recovery should all be baked in.
Cloud Data Solutions for Ransomware Prevention

Cloud storage and backup platforms can be powerful allies, if implemented correctly, and are central to effective cloud ransomware prevention and cloud backup & disaster recovery services.
- Immutable & versioned backups: Backups that can’t be altered or deleted protect against attacks targeting backup systems.
- Air-gapped or isolated backup storage: Store at least one backup copy disconnected from your primary network or in separate region/account.
- Frequent snapshots and incremental backups: As CrashPlan recommends, off-site cloud backups at intervals (e.g. every 30 minutes) reduce data loss risk.
- Cloud-native detection tools: Some cloud services now integrate AI-driven ransomware detection, which can stop suspicious encryption before it spreads (for example, Google is adding detection to Drive).
- Use backups as deterrents, not targets: Because attackers often go after backups, ensure backup systems themselves are monitored and protected.
Sentinel One’s cloud ransomware protection guidance emphasizes that organizations must harden backups in hybrid or full-cloud environments to block attack vectors.
Secure Backup & Recovery Methods
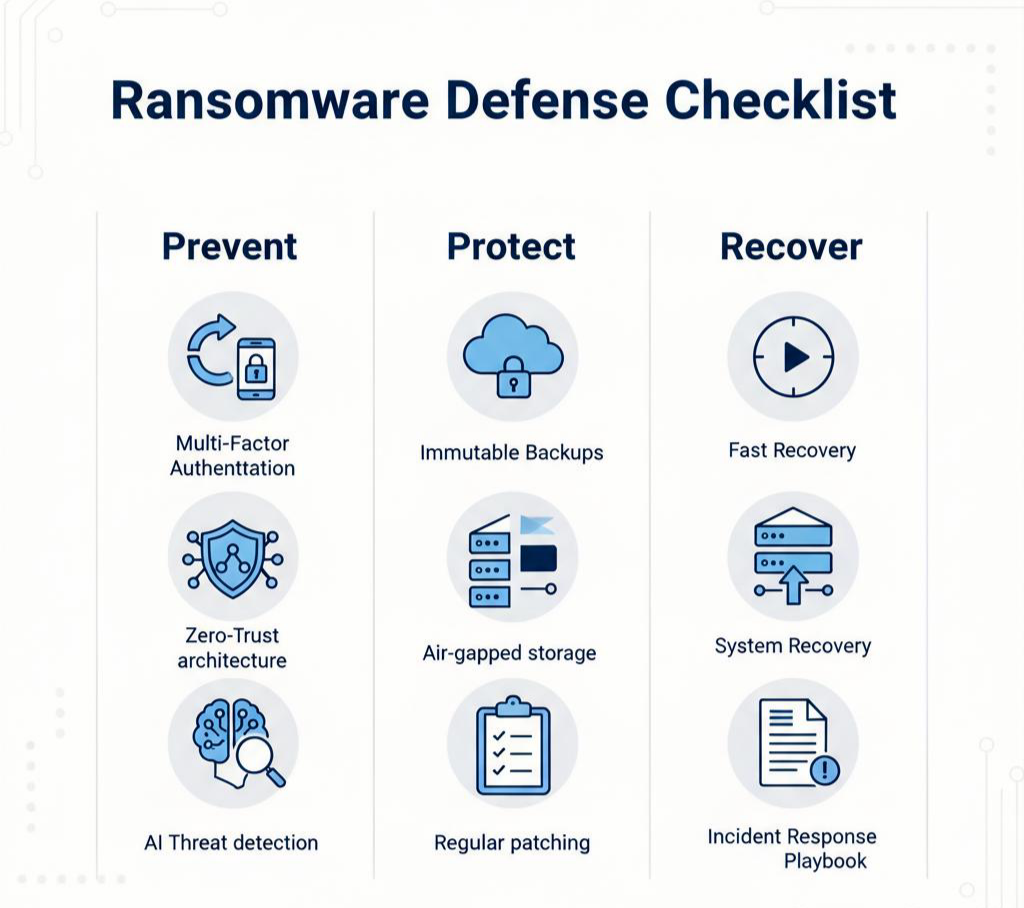
Your backups are your last line of defense. Here’s how to make them truly robust:
- Immutable, write-once storage: Prevent modification or deletion of stored backups.
- Multi-location backup & redundancy: Store backups across geographic sites or multiple cloud providers to reduce correlated risk.
- Frequent recovery tests: It’s not enough to back up; you must regularly restore in a clean environment to verify integrity.
- Separation of privileges: Ensure backup and recovery rights are isolated from day-to-day operations.
- Real-time or near-real-time backup designs: New research (e.g. ROFBS?) decouples backup operations from detection to reduce latency and improve reliability.
These practices help ensure that, even in the face of a full-blown attack, you can recover without paying ransom.
Frequently Asked Questions
What are the latest ransomware threats in 2025?
In 2025, attackers are evolving beyond simple encryption. We see AI-orchestrated attacks, faster breakout cycles, and higher use of data theft as leverage. Ransomware-as-a-Service ecosystems continue to grow, and niche groups like Ransom Hub, Qilin, or Akira have become more active.
How do Cloud Data Solutions protect against ransomware?
When built with immutability, air-gapping, frequent snapshots, and threat detection, cloud backup systems act as an offsite island, not just another target. Versions, isolation, and integrated encryption give you resilient recovery options and reduce reliance on paying attackers.
Should businesses pay ransom or use preventive strategies?
Paying ransom is never a reliable solution. Even when payments are made, you may not recover all data, and you fund criminal activity. In 2025, fewer organizations are paying: ITPro reports that just 17% of enterprise victims have paid ransoms. IT Pro Preventive strategies, backups, and response readiness are far better investments in the long run.
How can Data Security & Compliance reduce ransomware risks?
Compliance frameworks like GDPR, HIPAA, or industry standards push organizations to adopt encryption, audit trails, least-privilege access, and stronger governance. Being compliant often means having controls in place (access control, data classification, account auditing) that also deter ransomware attacks. Combining compliance with AI-driven security tools gives visibility, deterrence, and defensibility.
What’s Next; Acting with Purpose
Ransomware in 2025 is no longer about if, but when. The question is: how ready will you be?
- Audit your backup posture immediately: Can attackers delete it? Can you recover fast?
- Adopt or upgrade AI-driven detection tools behavior-based, sequence analysis, anomaly detection.
- Harden access and identity controls.
- Run “fire drills” simulate ransomware attacks and practice recovery steps.
- Consider working with experts or specialized security consultancies to build a roadmap that aligns with your regulatory and operational constraints.
You don’t have to wait for a breach to act. The more resilient your defenses, the less your organization is hostage to attackers.
Ready to strengthen your ransomware defenses?
Schedule a security assessment with our team to review your backup posture, cloud strategy, and AI-driven protection and turn this checklist into a concrete, actionable roadmap for your organization.
